
Karma-X Blog
HappyCamper: Doubling Down On Naming Space Location Randomization (NSLR)

Enter HappyCamper, a formal demonstration of the concept of "Naming Space Location Randomization - NSLR" for cyber defense.
HappyCamper is a tool which coins the term "Naming Space Location Randomization - NSLR" which formally demonstrates a particular aspect of "moving target defense" by empowering administrators to obscure the location of critical system binaries used by attackers, effectively adding a "filename password" that could stump adversaries relying on hard-coded paths.
The Example Of Address Space Layout Randomization - ASLR
Before the implementation of Address Space Layout Randomization (ASLR), attackers frequently exploited the predictable fixed locations of system libraries, such as Kernel32.dll on Windows, to execute malicious shellcode on vulnerable systems. Kernel32.dll, being a core Windows library that provides access to vital system functionalities, was a prime target because its APIs facilitated operations crucial for the execution of arbitrary code, such as creating processes or manipulating memory. The static memory address locations of these libraries and their exported functions enabled attackers to craft exploits with hardcoded addresses pointing directly to useful functions within these libraries. This method was particularly effective in buffer overflow attacks, where attackers could overflow a buffer with malicious input, achieve execution, and locate system api's to conduct operations with ease. The predictability of library locations drastically simplified the development of reliable exploits that could be reused across many systems.
The introduction of ASLR was a widespread mitigation technique which significantly increased the difficulty of such attacks by randomizing the addresses of loaded libraries and executables on each system, making the exploitation of such vulnerabilities considerably more challenging and requiring attackers to employ more sophisticated techniques to achieve reliable exploitation.
The principle here, summarized, was to randomize the location of system libraries and tell 'authorized code', but not 'unauthorized code'"
The Concept Of Living Off The Land And LoLBins
Living-Off-The-Land Binaries (LoLBins) represent a significant challenge in the field of cybersecurity, as they turn the very tools designed for system management and troubleshooting into weapons against the digital infrastructure they are meant to support. LoLBins are legitimate, native system applications that attackers exploit to execute malicious activities without having to introduce new malware into a target environment, thus evading detection by traditional security mechanisms. This exploitation is made possible through the abuse of built-in features or functionalities of these binaries, such as script execution, file transfer capabilities, or direct interaction with the system's underlying processes. PowerShell, with its powerful scripting capabilities and deep system integration, stands out as a prime example of a LoLBin. Attackers leverage PowerShell to conduct a wide array of malicious operations, from data exfiltration to system reconnaissance and beyond, all while masquerading their activities under the guise of legitimate system processes.
Enter NSLR - Randomizing Location Of Key System Libraries To Defend Against Living-Off-The-Land
Continuing from the foundation set by ASLR, HappyCamper introduces the concept of Naming Space Location Randomization (NSLR), which extends the principle of unpredictability to the filesystem level, specifically targeting LOLBin binaries.
How NSLR Works
NSLR works by allowing system administrators to rename critical system binaries like PowerShell, adding an unpredictable "filename password". This means that even if attackers can navigate a system's defenses and execute code, their reliance on the hardcoded paths to these LOLBins for further actions can lead them to a halt. Without knowing the new, randomized names of these binaries, their scripts and tools will fail to execute the intended malicious operations.
For example, by renaming powershell.exe to abc123_powershell.exe, any script or tool designed to utilize PowerShell by its default name will not find the executable, thwarting the attack attempt. This approach, while simple, adds a significant hurdle for attackers, especially those relying on automated tools and scripts that expect these binaries to reside at known locations.
Integrating NSLR with Traditional Security Measures
It's crucial to emphasize that NSLR, much like ASLR, is not a panacea for all security challenges. Instead, it serves as an additional layer in a multi-faceted defense strategy. The most effective security postures employ a layered approach, combining traditional measures such as endpoint protection, network security, access controls, and user education with innovative strategies like NSLR.
Moreover, the implementation of NSLR requires careful planning and communication within IT and security teams. System administrators must ensure that legitimate uses of renamed binaries are accounted for, updating scripts and tools to recognize the new names. This process may involve a period of adjustment, as users and automated systems adapt to the changes.
The Role of Security Telemetry and Alerting
An added benefit of NSLR is its potential to enhance security telemetry and alerting. Attempts to access the original, now nonexistent binary names can serve as a clear indicator of compromise (IoC). Monitoring systems can be configured to trigger alerts upon such attempts, allowing security teams to quickly detect and respond to potential attacks.
Striking Illustration Of The Power of HappyCamper
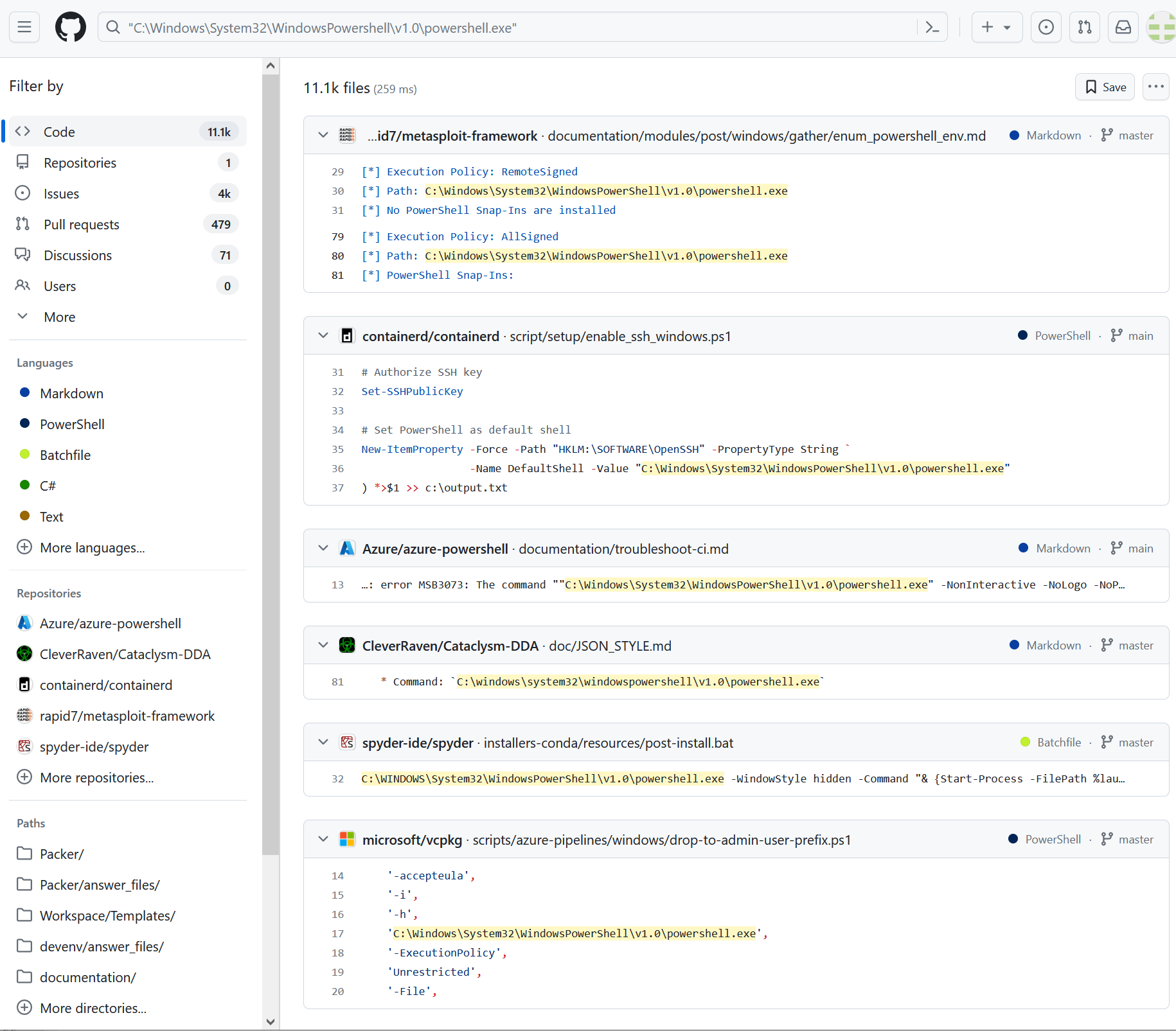
A striking illustration of this dynamic is the presence of over 11,100 hardcoded examples on GitHub, where both offensive and defensive tools exhibit references to "C:\Windows\System32\WindowsPowershell\v1.0\powershell.exe". This commonality underscores a significant vulnerability – the reliance on static, predictable paths to system binaries like PowerShell, which attackers and defenders alike exploit. For attackers, such hardcoded paths are gateways to executing malicious scripts and commands, leveraging PowerShell's extensive capabilities for nefarious purposes. The widespread occurrence of these references highlights a critical intersection: the tug-of-war between leveraging system tools for legitimate purposes and the potential for their misuse. It also emphasizes the necessity for innovative defensive approaches, such as HappyCamper's Naming Space Location Randomization (NSLR), to introduce unpredictability into system configurations, thereby complicating attackers' efforts to exploit hardcoded paths. After all, how hard is it for defenders to internally share the location of Powershell for authorized powershell scripts? The reader should be able to imagine the practical implications.
Conclusion - The Beginning Of Happy Camping With HappyCamper
HappyCamper emerges as a beacon of innovative defense, heralding the era of Happy Camping for system administrators and security teams. By introducing the concept of Naming Space Location Randomization (NSLR), HappyCamper not only amplifies the security posture of organizations through the concept of "moving target defense" and "security through obscurity", but also sets a precedent for the dynamic and adaptive defense mechanisms necessary in today's digital battleground. The tool's ability to obfuscate the paths to critical system binaries—a technique underscored by the glaring prevalence of hardcoded paths in both offensive and defensive tools on GitHub—serves as a critical countermeasure against attackers' reliance on predictability. HappyCamper exemplifies the kind of inventive strategies that will be paramount in thwarting attackers' efforts, ensuring that organizations can indeed look forward to many happy camping experiences in their security endeavors. This is not the end but rather the beginning where HappyCamper leads the way in setting a new paradigm of defense.
HappyCamper is available on Github, is free and open source software and will be extended and improved over time. Any and all feedback or input is appreciated!
Additionally, Karma-X offers its customers a version slightly ahead of the community version which adds additional protections to maintain an advantage. We’ll be adding optional registry modification in the next few days.
Further
The not so casual reader should come to understand that NSLR can be applied to api's, files, registry entries, configurations, and other system aspects. This concept can be applied to nearly anything that involves a sort of 'Naming Space".

From small business to enterprise, Karma-X installs simply and immediately adds peace of mind
Karma-X doesn't interfere with other software, only malware and exploits, due to its unique design.
Whether adversary nation or criminal actors, Karma-X significantly reduces exploitation risk of any organization
Update to deploy new defensive techniques to suit your organization's needs as they are offered