
Karma-X Blog
Indicator of Protection: Bringing Order to Chaos and Disrupting HAVOC C2

Sorry Havoc C2, better luck next time!
We came across this blog post yesterday claiming to defeat EDR's. We've heard a lot of this recently.
📖 Evading EDR: The Definitive Guide to Defeating Endpoint Detection Systems
Havoc C2 with AV/EDR Bypass Methods in 2024 (Part 1)
Claims to bypass AV/EDR with advanced evasion techniques
🎖️ To be totally fair to Sam Rothlisberger, who I believe is also a U.S. Army Officer (Thank you for your service!), Sam doesn't have access to Karma-X as Sam and the U.S. Army hasn't purchased it, yet.
Curiosity killed the cat, so let's just try this new "advanced EDR evasion" against Karma-X
Important Context: Karma-X has Yara and what not but that's not what we are relying on here, especially because Sam is specifically relying on different techniques to avoid signatures such as trying over and over again to evade detection against Windows Defender.
This is exactly the point of this blog of ours: Monopolies Fail in Cybersecurity: The Case for Small, Specialized, and Agile Platforms
We load up a TeamServer, add a listener, and launch a client:
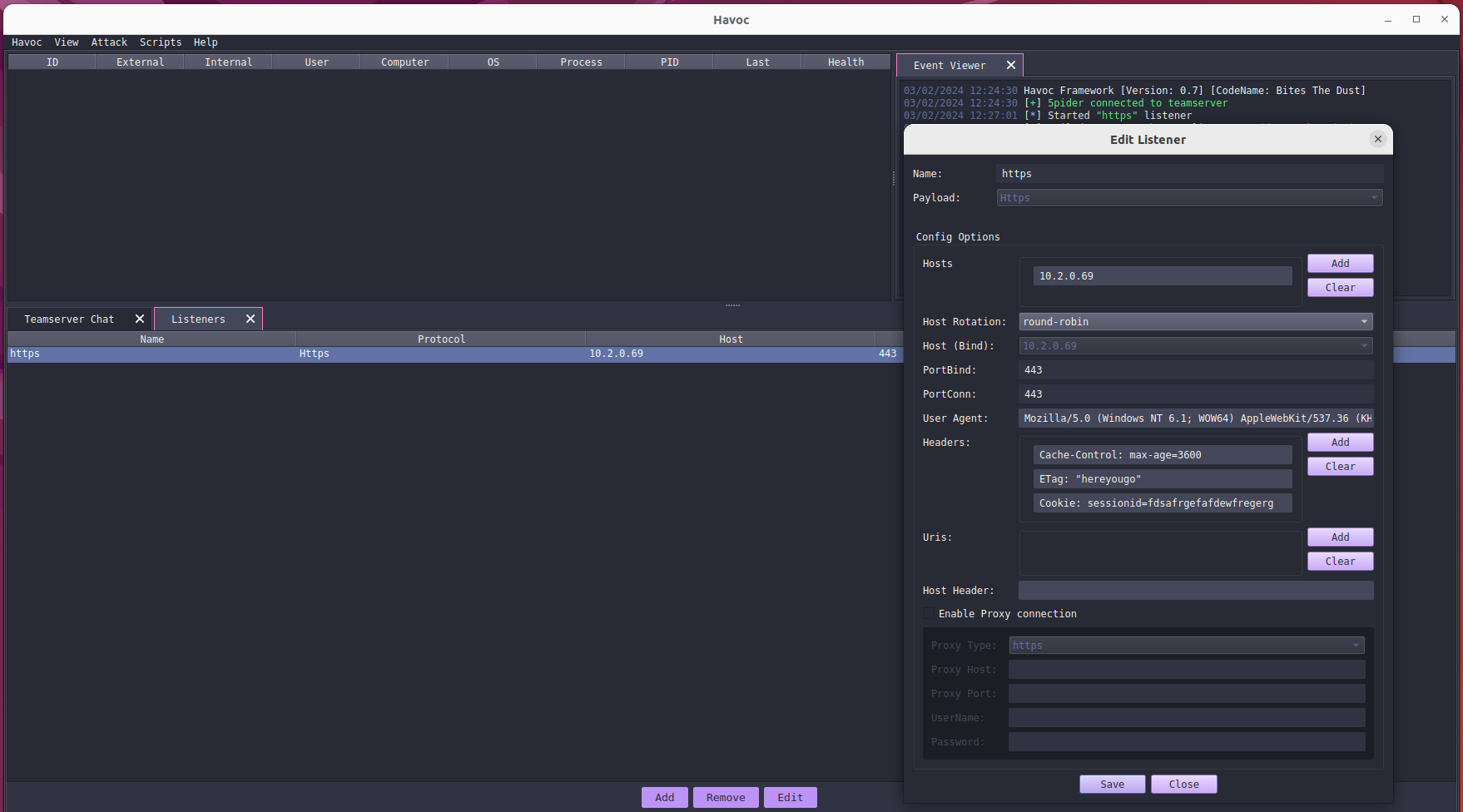
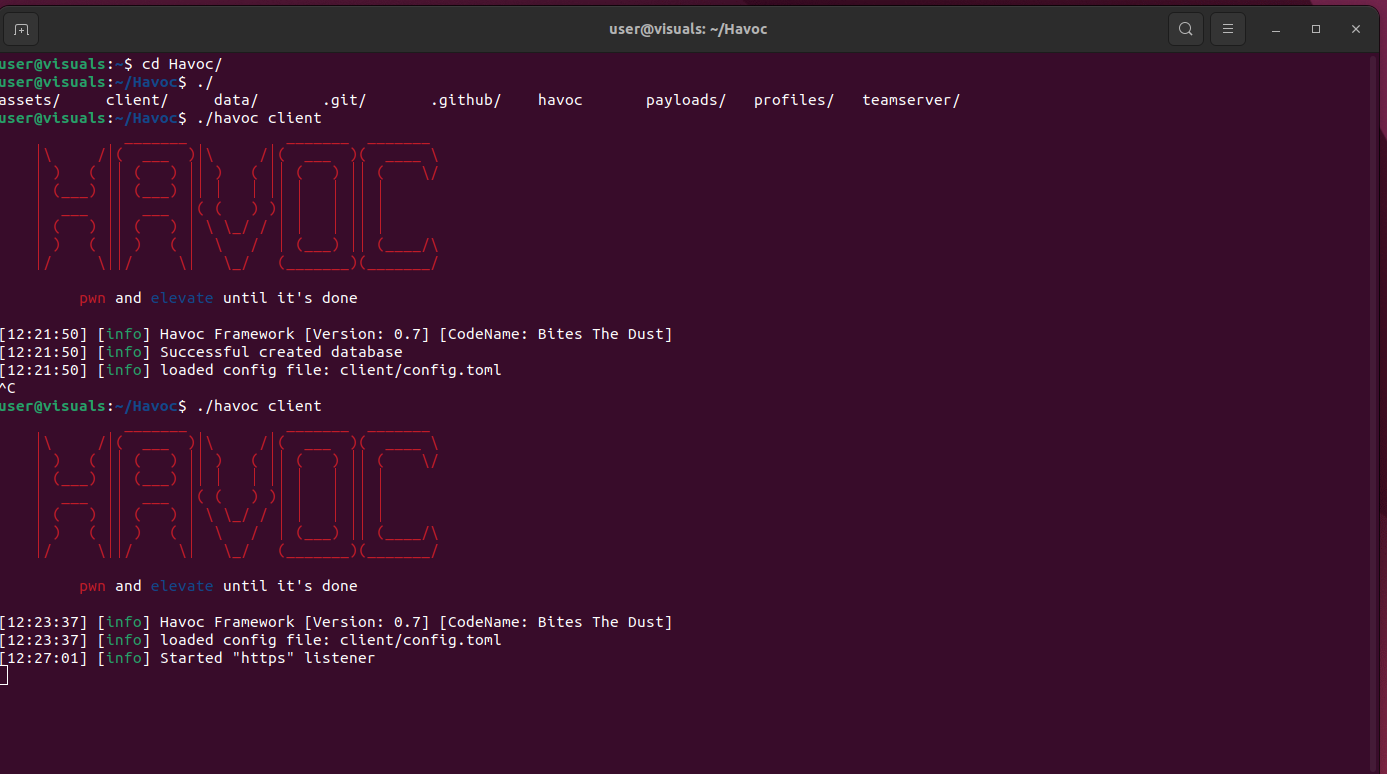
We generate demon.x64.bin with the exact same details from the blog with all the fancy AMSI and EDR evasions.
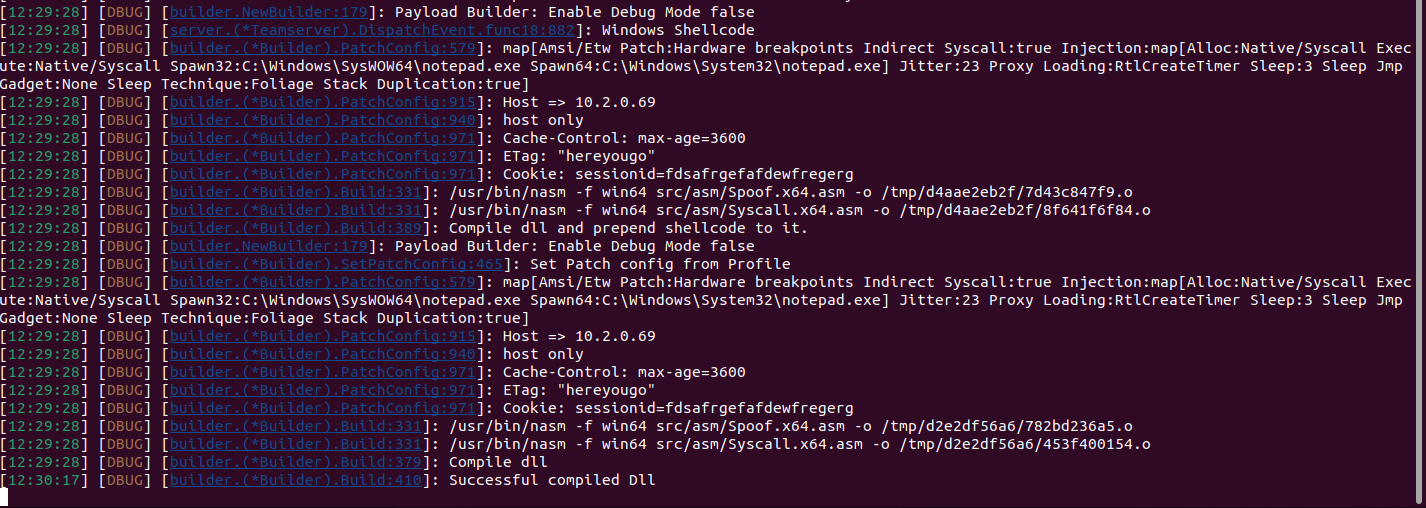
⚙️ Testing Assumptions:
In the interest of just getting down to it, we are just going to use a harness to see if any of this "advanced stealthy malware" can get past our defenses. Specifically, we just want to let it do its work.
There are a million and one ways to attempt to get your code loaded stealthily: encoders, packers, etc. Let's just assume they get its "arbitrary code" working. Karma has a test harness for that.
Ok, let's just load Havoc C2 into a Karma protected process. (no tricks, just execute the code)

Will the "advanced EDR evasion" work against Karma-X?
Whoops, attack not worky.
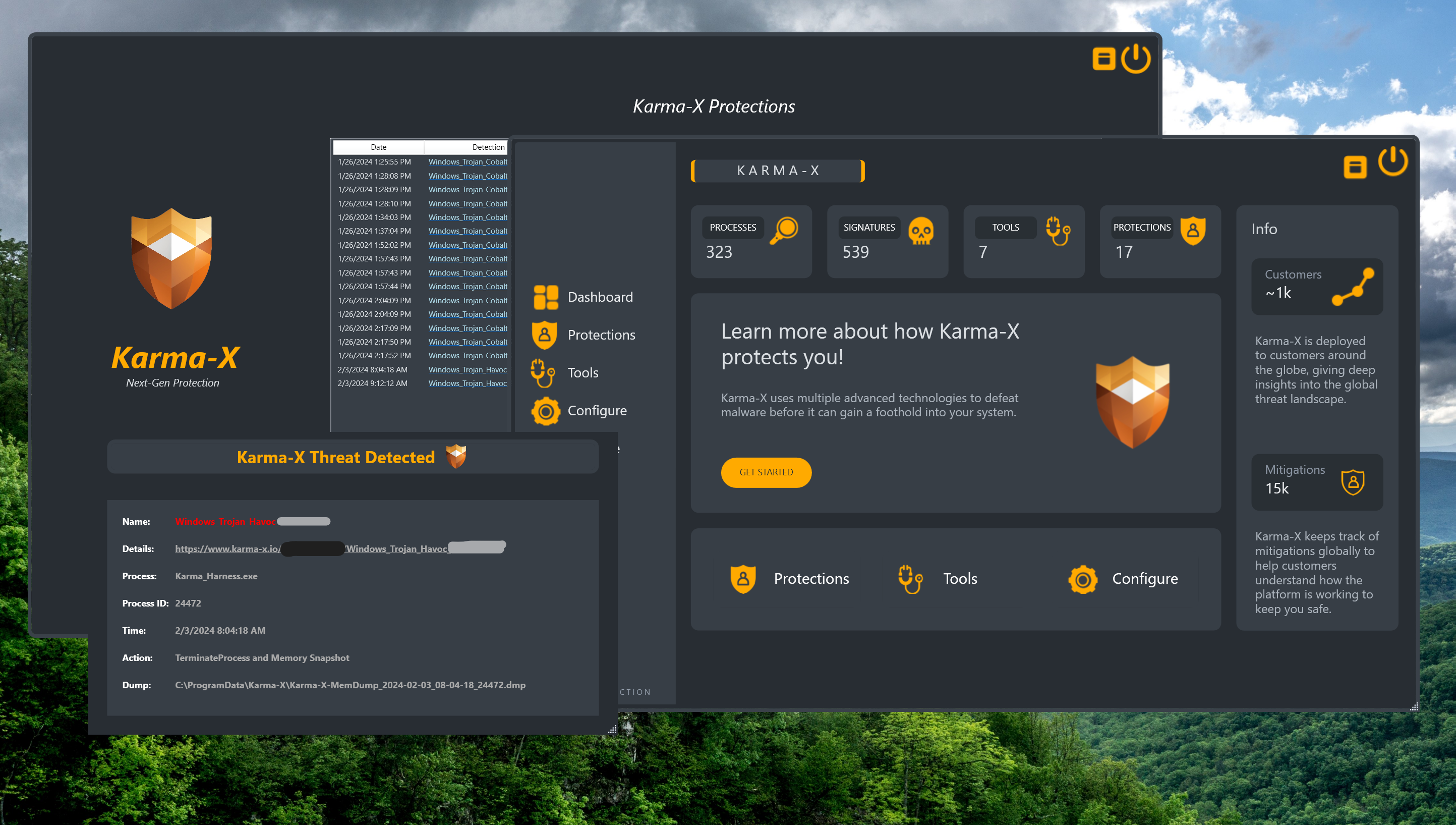
Even with all the fancy AMSI bypasses, EDR evasion techniques, and stealthy methods, Karma-X stopped the attack cold.
This is what true protection looks like.
Get Indicators of Protection for your systems today!
Access Vitamin-K Here!(after signing up and logging in)
From small business to enterprise, Karma-X installs simply and immediately adds peace of mind
Karma-X doesn't interfere with other software, only malware and exploits, due to its unique design.
Whether adversary nation or criminal actors, Karma-X significantly reduces exploitation risk of any organization
Update to deploy new defensive techniques to suit your organization's needs as they are offered